เว็บหวยออนไลน์ จ่ายจริง ราคาสูงส่วนลดเยอะต้อง แทงหวยออนไลน์ กับ เว็บหวย 999LUCKY เท่านั้น !
ขอยินดีต้อนรับทุกท่านเข้าสู่ ระบบ เว็บแทงหวยออนไลน์ชั้นนำอันดับ 1 ของไทย ที่มีเซียนหวย คอหวย เเละผู้คนเข้ามาใช้บริการเป็นจำนวนมาก ด้วยการบริการลูกค้ามานานกว่า 10 จึงการันตีได้ว่าเว็บเราเป็นเว็บชั้นนำระดับต้นๆของไทย 2020 !
999luckyเว็บแทงหวยอออนไลน์อินเตอร์ โดยเรามีบริการ แทงหวยออนไลน์ มี ระบบ ฝาก-ถอน รวดเร็ว เว็บแทงหวยเปิดให้บริการนานกว่า 10 ปี จึงมั่นใจได้ถึง ความปลอดภัยและมีมาตรฐานการบริการ 24 ชั่วโมง !!
โดยเฉพาะ หวยหุ้นออนไลน์ เราเป็นหนึ่งในผู้ให้บริการรับ แทงหวยหุ้น ที่ดีที่สุด มีหวยจากทุกประเทศ ออกผลตรงเวลา ไม่ต้องรอนานราคา อัตราจ่ายสูงที่สุด พร้อมโปรโมชั่นส่วนลดมากกว่าที่ไหนๆ เว็บแทงหวยจ่ายจริง ต้องเราเท่านั้น 999kuckyเว็บดีที่สุดในขณะนี้ 2020
เว็บแทงหวยออนไลน์ ชั้นนำอันดับ 1 ของไทย ที่จ่ายแพงที่สุด 2020
999lucky เว็บแทงหวยออนไลน์ ชั้นนำอัดดับ 1 ในเมืองไทย ที่มีผู้คน และ คอหวย ทั้งหลายให้ความนิยมเป็นอย่างมาก ในขณะนี้ เนื่องจาก เว็บมีระบบที่ทันสมัย สะดวก สบายง่ายต่อการใช้งานของลูกค้า และ ยังมีทีมระดับคุณภาพมืออาชีพไว้ คอยดูเเลตอบทุกคำถาม ทุกปัญหาลูกค้าอยู่ ตลอด 24 ชั่วโมง อีกด้วย ครับ !!
แถมทางเว็บเรายังมี กิจกรรม โปรโมชั่น มากมาย เพื่อให้สมาชิกได้เพลิดเพลิน กับทางเราอีกด้วยเพราะฉะนั้น ท่านใดที่ยังมองหาเว็บแทง หวยออนไลน์ อยู่ท่านไม่ควรพลาดเว็บดีๆอย่าง 999lucky ไปนะครับ !!
สมัครแทงหวย 999LUCKY วันนี้ ไม่มีค่า ใช้จ่ายใดๆ ทั้งสิ้น มิติใหม่ ของวงการหวยที่ดีที่สุด 2020
แทงหวยออนไลน์ 2020 กับเรา 999lucky จ่ายไม่ยั้ง ต้องการมั่งคั่งไม่รู้ตัว อย่ากลัวการแทงหวย ท่านจะได้พบกับ มิติใหม่ ของเว็บแทงหวยออนไลน์ ที่มีการแทงที่หลากหลาย แปลกใหม่ ต่างจากเว็บอื่นๆ
เเละแถมทางเว็บเรายังมี กิจกรรม โปรโมชั่น มากมาย เพื่อให้สมาชิกได้เพลิดเพลินกับทางเราอีกด้วยเพราะฉะนั้น ท่านใดที่ยังมองหา เว็บแทงหวยออนไลน์ อยู่ท่านไม่ควรพลาดเว็บดีๆอย่าง 999lucky ไปนะครับ >>ติดต่อเรา<<
สำหรับทุกท่านที่กำลังมองหา เว็บแทงหวยออนไลน์ จ่ายจริงไม่โกงเเละยังมีอัตราจ่ายแพงที่สุดในตอนนี้ เเละมีคนไทยนิยมเล่นมากที่สุด 999lucky จึงเป็นอีก 1 เว็บแทงหวยอีกนึงที่คนไทยหลายๆคน ให้ความไว้วางใจ มากที่สุด
ข้อดีของหวยออนไลน์ 999lucky
- ง่ายต่อการซื้อ เเละ แถมยังสะดวกสบาย
- เลขดังซื้อได้ไม่อั้น เเละ ยังสามารถซื้อได้ถึง 15.30
- หากถูกราลวัลระบบจะตัดเงินให้ทันที
- มีอัตราการจ่ายเยอะกว่า เว็บ อื่นๆ
- สำคัญ จ่ายจริง จ่ายไว ไม่โกงมั่นคงปลอดภัย 100%
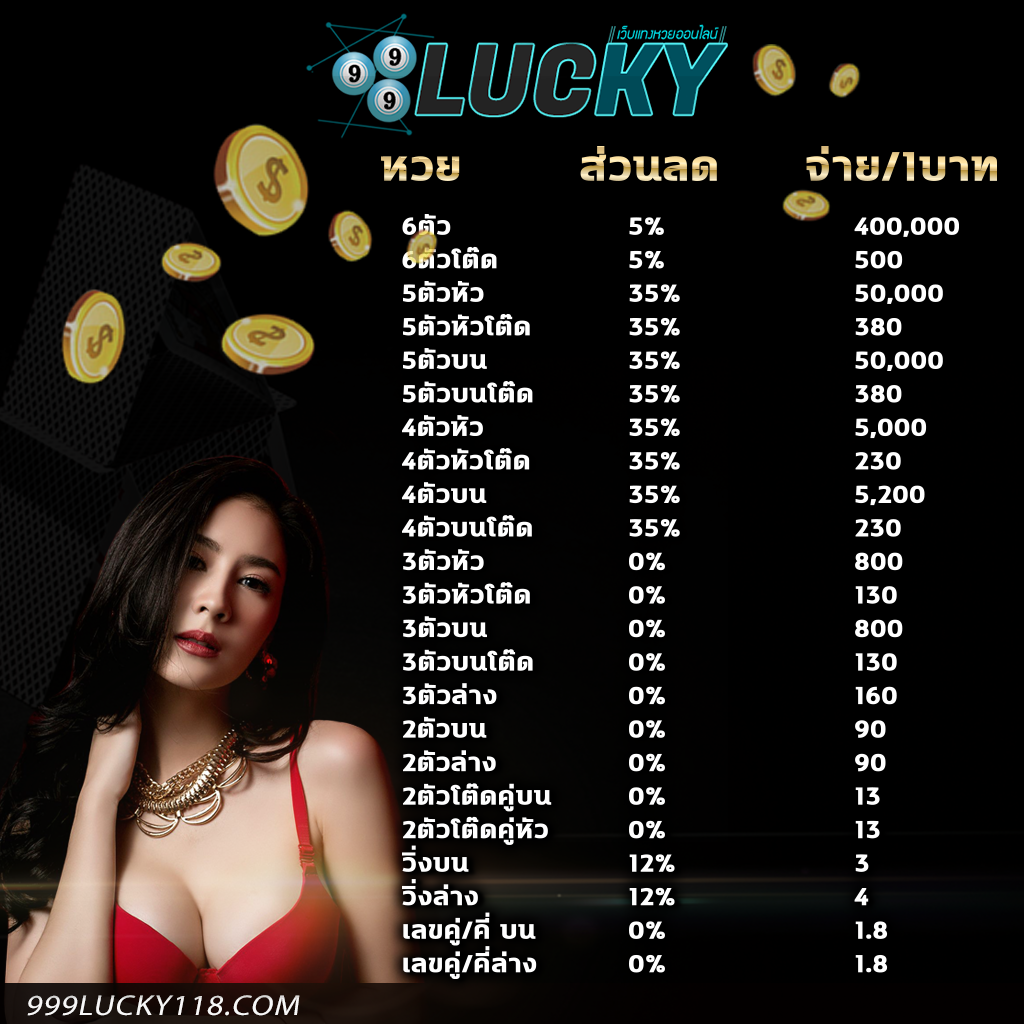
อัตตราการจ่ายเงิน เว็บหวยออนไลน์ 999LUCKY
โปรโมชั่นหวยลดสูงสุด 33% จ่ายมากที่สุด 550 แทงหวยปลอดภัยมั่นใจ
3 ตัว ลดสูงสุด 33% จ่าย 550 บาท
2 ตัวบนและล่าง ลดสูงสุด 28% จ่าย 70 บาท
3 ตัวล่าง จ่าย 125 บาท
วิ่งอัตราลด 12%3 ตัวโต๊ด จ่าย 105 บาท
2 ตัวโต๊ด จ่าย 12 บาท
แทงขั้นต่ำเพียง 10 บาทเท่านั้น
” สมัครฟรี ” วันนี้ลุ้นรับ สิทธิพิเศษ มากมาย จากทางเว็บพร้อม โปรโมชั่น สำหรับลูกค้าใหม่ เท่านั้นนะ ครับ
999LUCKYเว็บแทงหวยชั้นนำอันดับ 1 ของเมืองไทย
มั่นคง ปลอดภัย จ่ายจริง ไม่โกง ระบบ ฝาก-ถอน รวดเร็วทันใจ ต้องที่นี่ที่เดียวเท่านั้น
หวยรัฐบาล | หวยยี่กี | หวยฮานอย | หวยมาเลย์ | หวยออนไลน์